The Spot Method for Detecting Compromised Computers in a Network
Threats to computer network security are increasing, particularly regarding the “botnet” scenario where computers in a network are infected by malware programs (e.g., viruses, spyware, worms) that enable third parties to take control of the machines without the owners’ knowledge. Compromised computers, also known as “zombies,” can markedly decrease the efficiency of a network.
Current malware detection programs are only capable of detecting known malware agents; however, new malware is continuously being developed so that malware detection programs are chronically behind and require frequent updates. Additionally, most detection methods do not allow for the global monitoring of machines on a network.
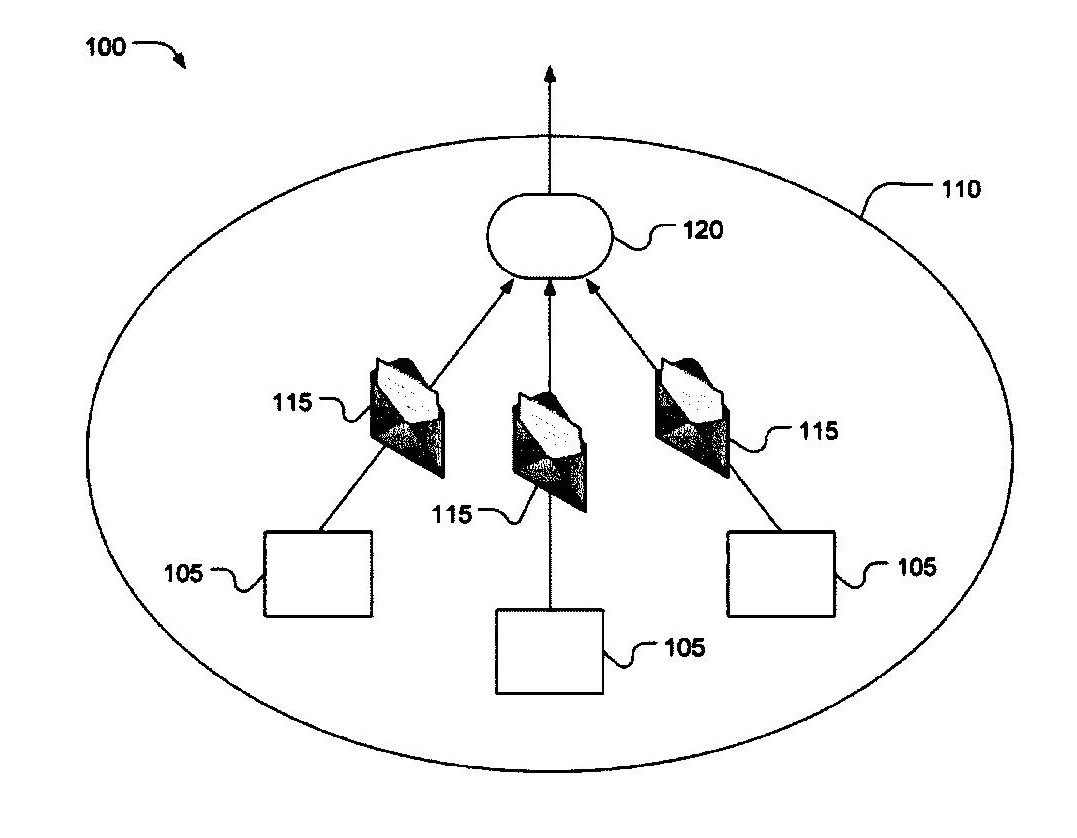
Unlike the current malware detection programs that focus on the point of infection, Dr. Duan has developed a new program, SPOT, that focuses on the number of outgoing messages that are originated or forwarded by each computer on a network to identify the presence of compromised machines. SPOT uses three algorithms that were specifically developed for the system. The first algorithm is based on the percentage of spam messages that originate or are forwarded from an internal machine. The second is based on the number spam messages that originate or are forwarded from an internal machine. The third is based on a statistical method called the sequential probability ratio test (SPRT). Importantly, SPOT analyses the total number of messages sent by a machine rather than only analyzing the rate at which they are sent to thwart spammers from purposely slowing the rate of message transmission in order to work around the system. The SPOT system enables individual networks to globally monitor computers on their networks and to automatically and accurately detect and efficiently remove compromised computers from their networks in an online manner. This novel detection method is applicable to a wide range of settings in which computer networks play an essential role.
Applications:
- Computer security industry.
- needing computer security (e.g., government agencies, financial institutions, research laboratories).
Advantages:
- May be incorporated into new or added to existing networks at low cost.
- Only a single copy of the SPOT software is needed to protect a network.
- Fills security holes left by existing malware detection programs that focus only on the point of intrusion.
- May be used in combination with other malware detection programs.
- Detects compromised computers quickly and accurately, with low false positive and false negative rates.